Written by Tim Cullen, CISSP, F5-CTS
Senior Security Architect at ADAPTURE
What is F5 Ticketbleed?
In late October, a vulnerability was discovered that affects all versions of F5 TMOS from versions 11.4 to 12.1. This was originally discovered by Filippo Valsorda of the Cloudflare Crypto Team. (You can read about how the vulnerability was detected by reading Filippo’s blog here). The vulnerability was given a CVE number of CVE-2016-9244 and labeled as an F5 TLS Vulnerability. The questions that our clients ask when a vulnerability is released are usually: “Are we vulnerable?”, “What is the impact?”, and “How do we fix it?” So, let’s go through these questions with the most important one first.
Are We Vulnerable?
To understand if you are vulnerable, you need to understand the attack. This vulnerability takes advantage of an SSL function called Session Ticketing. A TLS transaction will normally send out a session ID for tracking of the encrypted session.
As web pages have changed to frames and active code, the pages are now spawning multiple TLS sessions. This caused a slowness in the communication path. To help, Session Ticketing was added to speed things back up by allowing the session to be reused for the same source. So now a client TLS session ID is accompanied by a session ticket. The server will respond and accept the ticket. This validates the transaction and creates session tracking with a secure ticket. The Session ID typically has a range of 1 to 31 bytes of data. The F5 understands this structure and always creates a 32-byte response back to the client.
The vulnerability is in this communication exchange. The attacker will send a one-byte SSL Session ID connection request, and the F5 ends up responding with a 31-byte response of unused memory space. Multiply this times a few hundred thousand, and you could in effect cripple the memory of an F5. This attack is not necessarily against the SSL ticketing technology, but more how the F5 stack handles the communications.
So “Are we vulnerable?”…. The answer to that is really a two-fold question. Do we have session ticketing enabled on our Client SSL Profile settings, and what version of TMOS are we running? There is also a site that Filippo has created that helps a user test a URL to find out if it is vulnerable.
The default deployment of the Client SSL profile has Session Ticketing disabled. So, unless an F5 administrator physically turned this feature on, you are already protected. Below is the effected TMOS version list:
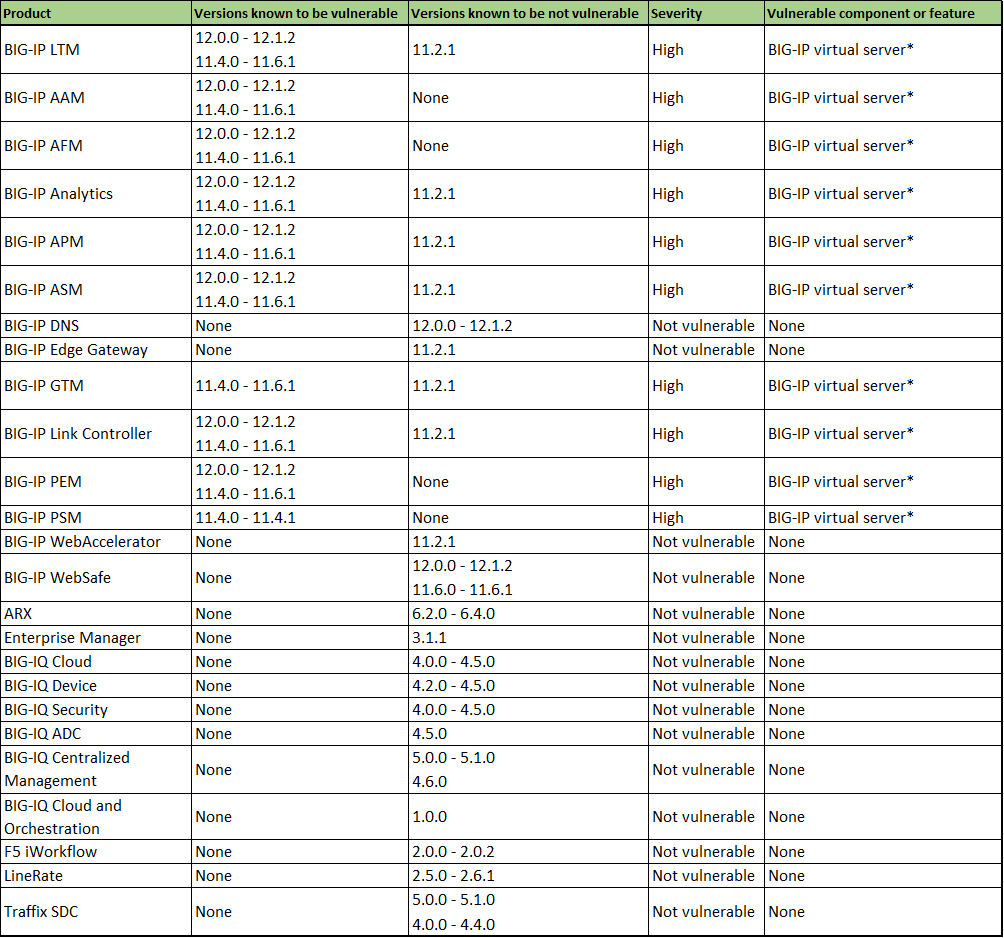
* The BIG-IP virtual server is associated with the Client SSL profile that has the Session Ticket option enabled.
What is the impact?
The impact to an F5, as discussed earlier, is the complete depletion of system memory, resulting in the device shutting down and effectively causing a denial of service on the vulnerable device. Keep in mind that this is not a default setting for the Client SSL Profile settings options.
How do we fix it?
If you find that you are indeed using the Session Ticket option in your Client SSL Profile settings, then the remediation is actually pretty simple and causes no impact to the F5 device. No reboot is needed, and any connected users will slow momentarily as the SSL connections are renegotiated with the client but should reconnect without incident. The following information is from the F5 Knowledgebase Article K05121675.
To mitigate this vulnerability, you can disable the Session Ticket option on the affected Client SSL profile. To do so, perform the following procedure:
Impact of action: Performing the following procedure should not have a negative impact on your system.
1. Log in to the Configuration utility.2. Navigate to Local Traffic > Profiles > SSL > Client.
3. For the Configuration option, select Advanced.
4. Clear the Session Ticket check box.
5. Click Update.
Please feel free to contact ADAPTURE if you have questions about developing your F5 roadmap. We’re F5 GUARDIAN partners (which means we are awesome at F5, as this is an exclusive partnership tier). I’m happy to join you for a whiteboarding session and eager to help you meet your goals.
Sources:
https://support.f5.com/csp/article/K05121675
https://filippo.io/Ticketbleed/
https://blog.filippo.io/finding-ticketbleed/












