The world of cloud storage is rapidly evolving. Organizations are moving to the cloud for its robust scalability, flexibility, and agility. As organizations move data to the cloud, they need to manage it efficiently while meeting strict compliance requirements. With NetApp’s new solution – Cloud Volumes ONTAP Managed Service [...]
Security Features in ONTAP 9 Datasheet
2022-10-13T20:01:22-04:00Security Features in ONTAP 9 Datasheet With the introduction of ONTAP 9, NetApp has continued to evolve its data management software with security as an integral part. The latest releases contain many new security features that are invaluable for your organization to protect its data across your hybrid cloud [...]
NetApp Data Migration Services Datasheet
2022-10-13T20:01:40-04:00NetApp Data Migration Services – Datasheet NetApp offers data migration services to help you get it right the first time. When moving from legacy storage environments, they offer proven methodologies and best practices to ensure fast deployment of your new SAN or NAS environment to minimize risk and disruption. [...]
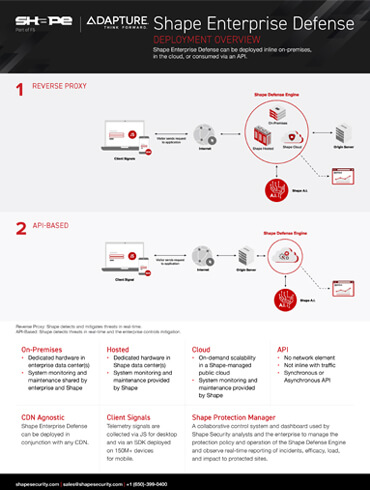
Shape Enterprise Defense Deployment Overview
2022-10-13T20:01:52-04:00Shape Enterprise Defense can be deployed inline on-premises, in the cloud, or consumed via an API Fill out the form to the right to download this datasheet and learn exactly how Shape Enterprise Defense can be deployed.
Credential Stuffing 2021: The Latest Attack Trends and Tools
2022-10-13T20:02:03-04:00Understand and Disrupt Sophisticated Attackers Who Retool Against Your Countermeasures From the stereotypical loner in the basement to organized criminal gangs and nation states, attackers have become increasingly sophisticated over the past decade. They have the same skills, tools, and services at their fingertips as your IT teams do. [...]
Attacker Economics
2022-10-13T20:02:20-04:00Understanding Economics Behind Cyber Attacks- What Makes Your Company a Prime Target? Automated attacks are proliferating against organizations around the globe. As the cost and investment of launching these attacks continues to plummet, companies are increasingly experiencing credential stuffing attacks that can lead to account takeover and fraud. Attackers [...]
Shape Enterprise Defense Solution Overview
2022-10-13T20:02:31-04:00Prevent sophisticated fraud and cyberattacks on web and mobile applications Web and mobile applications face an onslaught of sophisticated attacks with one commonality; instead of exploiting application vulnerabilities, attackers abuse an application’s functionality. Shape Enterprise Defense goes beyond traditional bot mitigation. By defending the world’s largest companies for multiple [...]
2021 Guide to Secure Remote Users
2022-10-13T20:02:41-04:00How to Improve Collaboration and Secure Network Operations For the Future Over the last year, companies around the globe rapidly deployed remote users with essentially little to no preparation. Following 2020,72% of organizations expect greater resilience and agility to be byproducts of the pandemic experience. Most organizations do not [...]
Ease Your IT Burden with Intelligent Storage
2022-10-13T20:02:51-04:00Eliminate Manual Storage Troubleshooting with AI and Predictive Analytics Today’s IT managers are spending more time managing storage volumes than actually optimizing data for business advantage. With 31% of IT teams spending 21 hours (and sometimes more) a week on data housekeeping, your critical engineers are being kept away [...]
Supporting SHA1 and SHA2 in the Same Virtual Server
2023-08-31T10:20:38-04:00Supporting SHA1 and SHA2 in the Same Virtual Server Using F5 Networks’ Local Traffic Manager A Whitepaper by Adapture F5 CTS This whitepaper explains the design behind the support for SHA1 and SHA2 within the same virtual server using F5 Networks’ Local Traffic Manager and illustrates the steps necessary [...]